PATCH AND PROTECT ASAP!!!
External RDP connection to Non-NLA RDP Windows Enabled NOT ADVISED
http://technet.microsoft.com/en-us/security/bulletin/ms12-020
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2012-0002
Overview
The Remote Desktop Protocol (RDP) implementation in Microsoft Windows XP SP2 and SP3, Windows Server 2003 SP2, Windows Vista SP2, Windows Server 2008 SP2, R2, and R2 SP1, and Windows 7 Gold and SP1 does not properly process packets in memory, which allows remote attackers to execute arbitrary code by sending crafted RDP packets triggering access to an object that (1) was not properly initialized or (2) is deleted, aka "Remote Desktop Protocol Vulnerability."
Impact
CVSS Severity (version 2.0):
CVSS v2 Base Score:9.3 (HIGH) (AV:N/AC:M/Au:N/C:C/I:C/A:C) (legend)
Impact Subscore: 10.0
Exploitability Subscore: 8.6
CVSS Version 2 Metrics:
Access Vector: Network exploitable
Access Complexity: Medium
Authentication: Not required to exploit
Impact Type:Allows unauthorized disclosure of information; Allows unauthorized modification; Allows disruption of service
Pre-auth, network accessible, service running as SYSTEM
This issue is potentially reachable over the network by an attacker before authentication is required. RDP is commonly allowed through firewalls due to its utility. The service runs in kernel-mode as SYSTEM by default on nearly all platforms (except for one exception described below). During our investigation, we determined that this vulnerability is directly exploitable for code execution. Developing a working exploit will not be trivial – we would be surprised to see one developed in the next few days. However, we expect to see working exploit code developed within the next 30 days.
The good news is that the Remote Desktop Protocol is disabled by default, so a majority of workstations are unaffected by this issue. However, we highly encourage you to apply the update right away on any systems where you have enabled Remote Desktop.
Workaround option: Enable Network Level Authentication (NLA) on Windows Vista and later platforms
There is something you can do to substantially reduce the risk on Windows Vista and later systems where RDP is enabled: You can enable Remote Desktop’s Network Level Authentication (NLA) to require authentication before a remote desktop session is established to the remote desktop server. On systems with NLA enabled, the vulnerable code is still present and could potentially be exploited for code execution. However, NLA would require an attacker to first authenticate to the server before attempting to exploit the vulnerability.
A Closer Look: MS12-020 Remote Desktop Vulnerability
Useful reference information about McAfee products
In the March Patch Tuesday release, Microsoft issued MS12-020, which addressed a critical vulnerability in Microsoft Remote Desktop, which has all the right characteristics needed for a self-propagating worm The SANS Internet Story Center went so far as to raise their Infocon level to ‘Yellow’ for the first time since 2010, as a direct result of the potential risk associated with this vulnerability. Though McAfee has not yet seen widespread attacks or malware in the wild, a few preliminary proof-of-concept exploits have surfaced, including a module for the popular Metasploit penetration testing framework. While we wait for more data, RDP merits additional attention over the coming weeks. Scott Taschler, McAfee Solutions Architect, examined the RDP events in more detail.
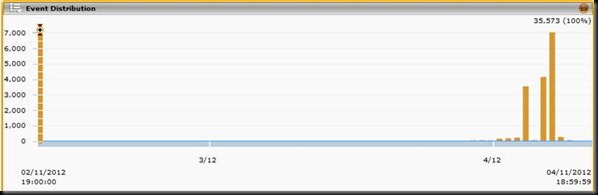
“I took a look at my own small lab network and what I saw was eye opening. Below is a chart from my Nitro SIEM, showing a pretty dramatic spike in inbound RDP events over the last two weeks. Note that there was almost NONE prior.
“Most of these are blocked firewall connections, with a smattering of other things:
“While this isn’t cause for alarm, it could indicate a potential surge on the horizon. Customers are advised to (1) use network-based access controls to block RDP access where it’s not needed; (2) use network IPS to watch for emerging threats and block them proactively; and (3) deploy the patch!”
McAfee Labs is performing additional research. When details are available, you’ll find them on the McAfee Threat Center.